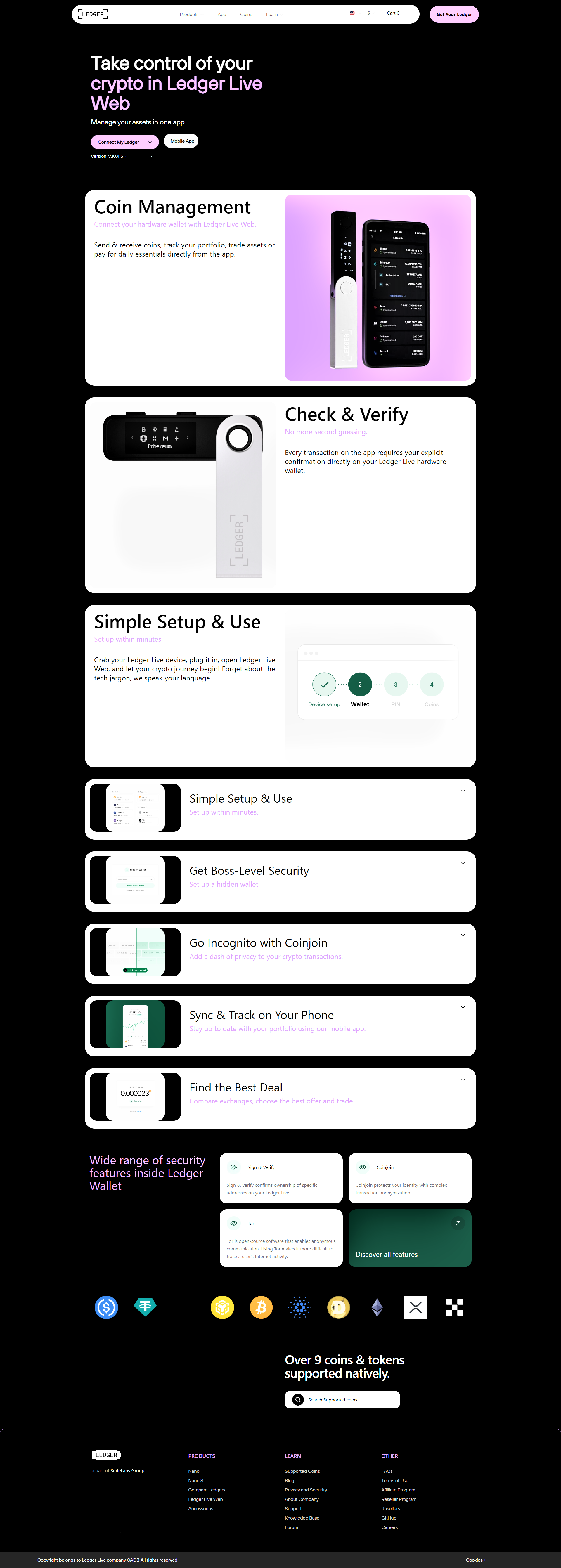
Ledger Login: The Ultimate Guide to Secure Access & Safe Crypto Management
In the fast-growing world of cryptocurrency, security and control are not just options—they’re essential. If you're serious about protecting your digital assets, you need a secure way to manage them. That’s where Ledger comes in, offering industry-leading hardware wallets like the Ledger Nano S Plus and Ledger Nano X. These wallets rely on a secure and simple yet highly effective process known as the Ledger login.
In this comprehensive guide, we’ll cover everything you need to know about the Ledger login process—what it is, how it works, why it matters, and how it compares to other wallet login methods. Whether you're new to crypto or a seasoned investor, this article is tailored to help you maximize the security of your Ledger wallet.
🔐 What is the Ledger Login?
Ledger login refers to the authentication process required to access your Ledger hardware wallet using the Ledger Live app. It involves verifying your identity by:
- Physically connecting your device (Nano S Plus or Nano X)
- Entering your unique PIN code
- Manually confirming actions on your Ledger device
This login method ensures that even if your computer is compromised by malware, your private keys remain secure and offline.
🛠️ Step-by-Step: How to Log In to Ledger
Logging into Ledger is straightforward yet highly secure:
-
Connect Your Device
Plug your Ledger wallet into your computer via USB or pair it with your smartphone using Bluetooth (for Nano X). -
Open Ledger Live
Launch the official Ledger Live app—available for Windows, macOS, Linux, iOS, and Android. -
Enter PIN Code
Input your secure PIN directly on your device. This unlocks access to your private keys without exposing them online. -
Confirm Device Identity
When accessing apps or signing transactions, physically approve them using your Ledger device. -
Access Wallet Dashboard
Once logged in, you can check your balance, manage apps, view transactions, and securely send or receive crypto.
🛡️ Why Is the Ledger Login Process So Secure?
The strength of Ledger login lies in cold storage combined with physical confirmation. Unlike software wallets or exchanges that store keys online, Ledger stores your private keys in a secure element chip, disconnected from the internet. Hackers cannot access your funds unless they have physical access to your device and know your PIN.
Key security features include:
- PIN Code Protection
- Recovery Phrase (24 words)
- Firmware Security Updates
- Two-Level Verification (Device + App)
💡 Ledger Login vs. Other Crypto Login Systems
FeatureLedger LoginWeb-Based WalletsMobile App WalletsPrivate Key StorageOffline (Cold)Online (Hot)Online (Hot)Malware ResistanceVery HighLowModeratePhysical AuthenticationYesNoSomeRecovery Phrase BackupYes (24 Words)OptionalYes (but online)Ideal for Large Holdings?✅ Yes❌ No⚠️ Risky
Ledger stands out as the most secure login solution for long-term storage and high-value crypto portfolios.
🔧 Common Ledger Login Issues & Fixes
Even secure systems can run into technical issues. Here are quick solutions:
🔄 Device Not Connecting?
- Use a different USB cable or port
- Reboot your device
- Ensure you’re using the official Ledger Live app
🔑 Forgot Your PIN?
- Reset the device using your 24-word recovery phrase
📱 Bluetooth Not Working (Nano X)?
- Re-pair the device through your phone’s Bluetooth settings
- Ensure permissions are granted for the app
✅ Best Practices for a Safe Ledger Login
To make the most of your Ledger wallet, follow these tips:
- Only use official apps from www.ledger.com
- Keep your PIN and recovery phrase secure—never store them online
- Update Ledger Live and firmware regularly
- Enable password lock on the Ledger Live app
- Use a separate device for crypto transactions if possible
📲 Using Ledger Login on Mobile
With the Ledger Nano X, you can manage your crypto portfolio on your smartphone. The Ledger Live mobile app allows you to:
- Check balances
- View transaction history
- Send or receive coins
- Manage installed apps
Tip: Use biometric security on your phone in addition to your device's PIN for extra protection.
❓ Frequently Asked Questions (FAQs)
Q1: Can someone hack my Ledger wallet during login?
A: No. Since Ledger devices require physical confirmation, a hacker cannot access your funds without the device and your PIN.
Q2: Is Ledger Live login the same as Ledger device login?
A: Not exactly. Ledger Live is the interface, while your actual security lies in the physical Ledger hardware wallet.
Q3: What happens if I lose my Ledger device?
A: Simply get a new Ledger and restore access using your 24-word recovery phrase.
📝 Final Thoughts: Why Ledger Login Matters
The Ledger login process is much more than just entering a password. It is a robust security gateway that separates you from hackers, phishing attacks, and malware. In a digital world where cryptocurrency theft is increasingly common, Ledger’s combination of offline protection and physical authentication stands as the gold standard.
Whether you’re investing a few hundred or millions in crypto, your Ledger wallet—and the way you log in—could mean the difference between total control or complete loss of your assets.